3 Worst Email Scams Targeting Small Businesses, and How to Avoid Them
Updated
We’ve all heard about big companies being hacked (Equifax, Marriott, Uber, Yahoo, etc.), but cyber criminals are increasingly targeting businesses with scams that don’t involve hacking at all. Rather than finding and exploiting technical vulnerabilities in online systems, these attacks use targeted emails to fool people into doing the work for them.
Small businesses are especially at risk for this type of cyber attack. According to Symantec’s 2019 Internet Security Threat Report, employees of small organizations were more likely to be hit by email threats—including spam, phishing, and email malware—than those in large organizations. Here are three of the top email threats for small businesses, and how to guard against them.
Spear Phishing Emails
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and financial information by emailing someone while pretending to be a trusted entity such as an employee, relative, friend, or business associate.
According to the 2020 State of the Phish Report, 65% of U.S. organizations experienced a successful phishing attack last year, resulting in loss of data, credential or account compromise, ransomware infection, financial loss, or wire transfer fraud.
The most common, and most successful, form of phishing is spear phishing. Spear phishing is a more targeted phishing attempt in which cyber criminals gather information about their targets and use it to trick them into providing information they can use to steal money or sensitive information. According to the 2020 State of the Phish Report, 88% of organizations were the target of spear phishing attacks in 2019.
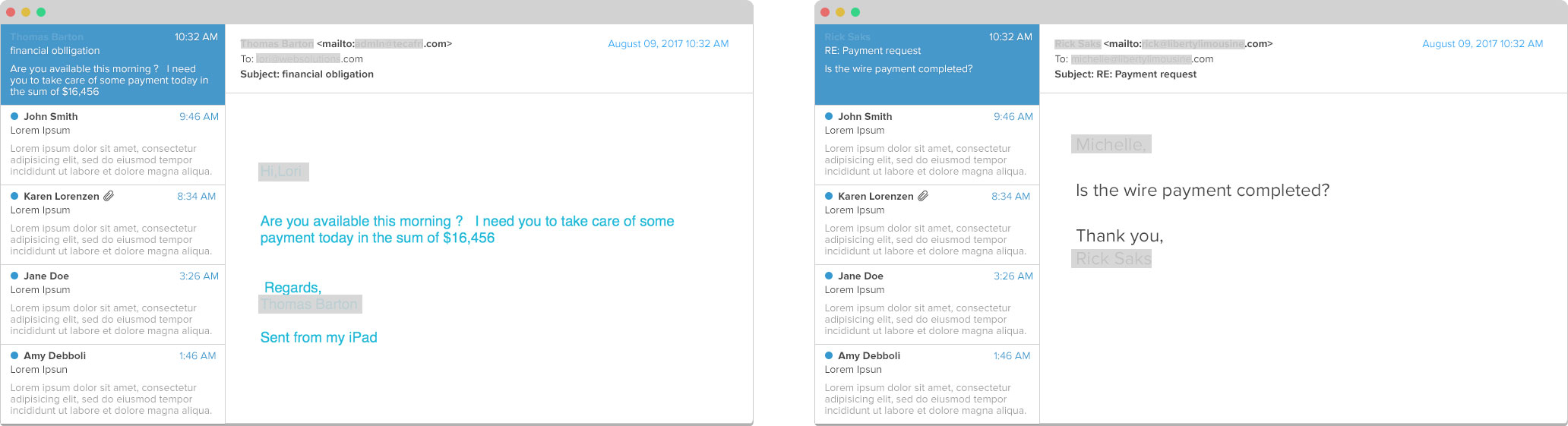
For instance, a cyber criminal might visit your website, see a company you identify as a partner, go to that company’s website, find a list of employees that work there, email you pretending to be the partner company’s president, and ask you to provide sensitive information, perform an action that will give them access to your accounts, or even wire money directly to them.
Spear phishing is often successful because the email and the sender feel familiar, so they don’t raise suspicion. In addition to appearing to be from someone you know and trust, a spear phishing email will often have a familiar greeting, and might even reference something personal about you that a fraudster has found on social media or a Google search, such as a “mutual friend” or personal or professional details.
If you receive an email that seems like it’s from someone you know, but that you weren’t expecting or that makes an unusual request, hover over the sender name to see the return address. If that mailto: address doesn’t match the email you have in your contacts, do not reply, and make sure you notify your IT department and the person whose identity is being used. If any email raises your suspicions (i.e., uses strange wording or has a tone inconsistent with previous emails from the supposed sender), call the individual to confirm the request.
Fake Email from a Real Company
Another type of email scam seems to come from a company you know and trust, such as a bank or credit card company, or others such as PayPal, Amazon, or Netflix.
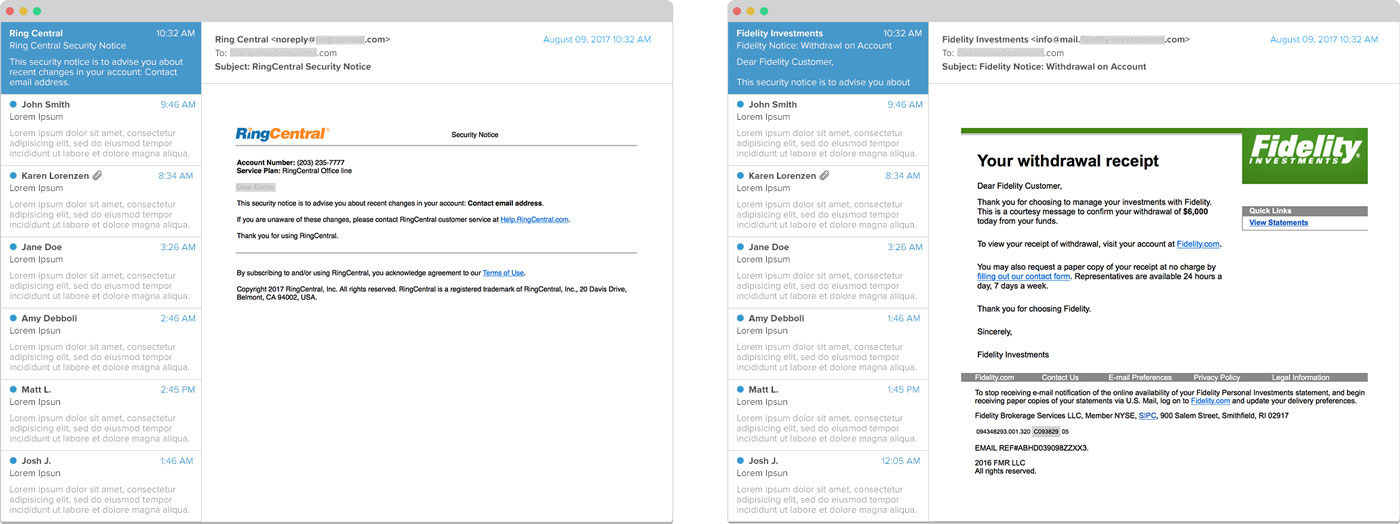
The email will ask you to click a link in the email to accomplish some “required” task. These types of emails often try to overcome any hesitation or suspicion on the recipient’s part not only by pretending to be company you recognize, but by making the requested action seem urgent, like saying you will lose access to an account unless you update your information. Ironically, some of these emails actually ask you to update your password to guard against a computer virus or hack attack.
If you click the link, you’ll be taken to a fake website that may look very similar to the actual website, but will actually be set up to steal the information you enter.
Never click a link in an email unless you are sure it comes from a reputable source. Hover over the link to see where it would take you. Fake links will often have a URL that is similar to the actual website, but slightly different, such as accounts.trustedcompany.net rather than www.trustedcompany.com, or it might even be a totally unfamiliar URL name with a long string of extra characters. In either case, the site is a spoof website.
If you think the email is legitimate and you click the link, look at the website carefully before entering information. Check the URL address bar to see if the official name of the company appears, check for the https://, and look for spelling and grammar errors and unusual or clumsy phrasing. If you have any doubt that it’s a legitimate site, close your browser immediately. In rare cases, the fake URL may be indistinguishable from the real one—to double check, cut and paste the URL into a new browser window. If the URL in the new window is different that the one you saw, it’s fake.
Even better, if you ever receive an email from a company, instead of clicking the link, open a separate browser window and enter the known URL of the company to be sure you’re on the right site.
Malware
Malware, short for “malicious software,” is a software program designed to infiltrate your computer to do damage, including stealing data, disabling systems, deleting or corrupting files, or even spying on you. Viruses, Trojan horses, ransomware and worms are all types of malware. All take different approaches, but all are very dangerous for a small business.
Though you can also come into contact with malware by visiting an infected website or plugging an infected device into your computer, malware is more frequently transmitted through email, either in an attachment or a link within the email itself. According to the 2019 Data Breach Investigation Report from Verizon, 94% of malware is delivered through email phishing.
If you receive a questionable email with an attachment, be especially cautious if the attachment is a Microsoft Office file. According to the 2019 Internet Security Threat Report, 48% of malicious email attachments are Microsoft Word or Excel files with extensions including .doc, .dot, .docx, .dotx, .docm, .xls, .xlt, or .xlsx. Other dangerous files include those that end with .exe, .rtf, .jar, .vbs, and .pdf.
If you do not recognize the sender, do not open the attachment under any circumstances. If you recognize the sender but are not sure an attachment is legitimate (or you just want to be safe), contact the person who sent the email.
Though having spam filters and up-to-date antivirus software is always a good idea for any small business, email attacks work so often because rather than focusing on technical weaknesses, they exploit human error. Attack channels and approaches are always changing and evolving, so the best defense is to err on the side of caution—if something seems off, it probably is.